Ponemon’s State of Password Security Recap
Security breaches have become alarmingly common — both at home and in the workplace. Despite the rise of two-factor authentication and constant horror stories in the media, many people still have poor password hygiene and remain at risk for these kinds of attacks. The stakes are even higher for small businesses with many employees — a single data breach could put them out of business.
The Ponemon Institute, a leading provider of independent research on data protection and emerging technologies, recently released its 2019 State of Password and Authentication Security Behaviors Report. The survey of 1,761 IT and IT security practitioners around the world provides a lot of insight into privacy and security concerns, including password management, authentication strategies and cybersecurity costs.
Let’s take a look at some of the key insights from the report and some best practices to help address them.
Table of Contents
Phishing Attacks are Common
Phishing attacks have become the most popular form of cyberattack against many homes and businesses. According to Ponemon, more than half of respondents (51 percent) said that they have experienced a phishing attack. A separate survey from Cloudmark found that phishing attacks were responsible for 38 percent of all cyberattacks on respondent companies and the average cost following an attack was upwards of $1.8 million.
Surprisingly, 57 percent of those that experienced a phishing attack didn’t change the way that they manage their passwords. There’s a good chance that many of these incidents also go unreported in the workplace. It’s important to train employees on how to recognize phishing attacks and encourage them to report any attacks to the proper IT personnel. These efforts can help inform training exercises and proactively address risks.
Many network security solutions can also help prevent many phishing attacks. For example, Jungle Disk's Active Network Protection provides cloud firewall protection, safe internet filters, VPN remote access and secure WiFi for employees and guests. By blocking many common phishing attempts before they reach employees, you can reduce the changes of employees inadvertently becoming a victim to these kinds of attacks.
Password Hygiene is Lacking
Poor password hygiene is a leading cause of cybersecurity problems. According to Ponemon, nearly 70 percent of respondents have shared passwords with colleagues in the workplace and more than half reuse an average of five passwords across their business and/or personal accounts. Two-factor authentication can mitigate many of these issues, but nearly 70 percent of respondents don’t use two-factor authentication.
Download a sample cybersecurity job posting to use as a template during your hiring efforts.
There are several best practices that can help:
-
Update passwords on a regular basis because stale passwords often show up in data breaches over time.
-
Use passphrases rather than passwords because they’re longer and harder for computers to crack.
-
Use different passwords for each website or service, so if one is compromised, it doesn’t impact other areas.
-
Enable two-factor authentication or use hardware tokens to add a second layer of security to your sensitive accounts.
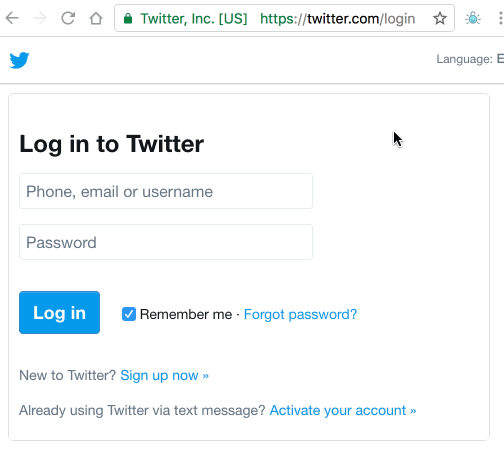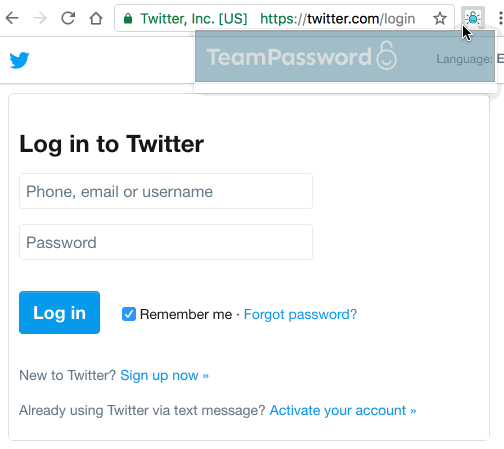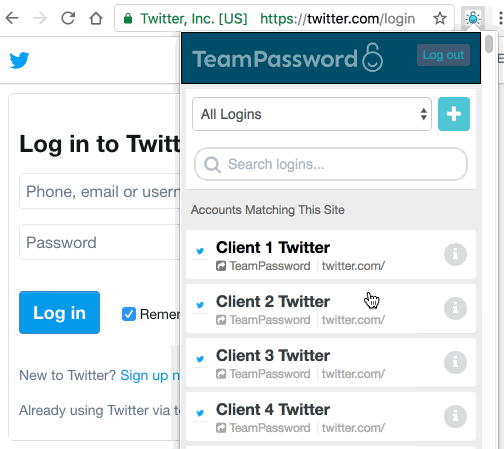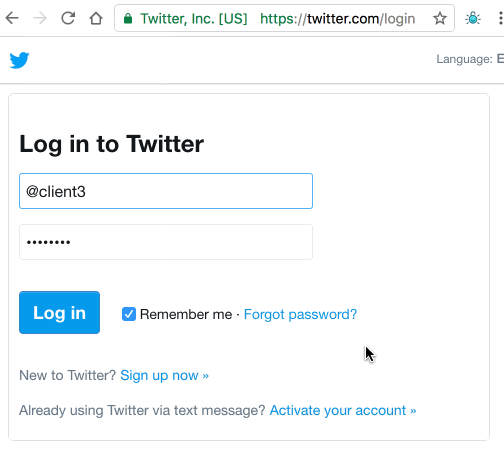
Password managers, like TeamPassword, make it easy to automatically generate strong passwords and securely share them with colleagues. With browser plugins, TeamPassword even makes it easy to auto-fill strong passwords, so employees don’t have to remember them or look them up every time. That way, there’s no excuse for employees to share passwords with their colleagues or re-use the same password across multiple services.
Managing Passwords is Costly
Many small businesses know the importance of proper password management, but they may not realize how much it costs to manage passwords. According to Ponemon, the average respondent spends about 12 minutes per week entering and/or resetting passwords. This translates to an average cost of $5.2 million per year in lost productivity for organizations with 15,000 employees — and significant sums for any smaller businesses.
Password managers can help reduce these costs by making it easier to generate and auto-fill passwords. TeamPassword even makes it easy to share common passwords between employees and eliminates the need for password spreadsheets or other bad practices. With the average team having nearly 150 passwords to manage, the ability to generate unique passwords and share them can have a big impact on productivity.
Sign up for a free 14-day trial of TeamPassword today!
Hardware Tokens Are the Future
Managing passwords can be inconvenient and cumbersome, and it’s impossible to ensure that every single employee is following these best practices. It only takes a single rogue employee or insecure password to bring down the entire network. According to Ponemon, 56 percent of respondents believe that physical hardware tokens are a great alternative to two-factor authentication by eliminating the need for a smartphone or tablet.
Hardware tokens are physical devices that you carry with you or plug into your computer or smartphone. Some of these devices provide a one-time passcode for signing in with two-factor authentication while others interface directly with common applications, including email and social media accounts. Most of these devices still require a password, but employees don’t need to worry about using a smartphone or requiring WiFi.
There are also some attempts to remove passwords altogether. For instance, Apple’s Face ID uses biometrics to unlock the smartphone and make purchases. These technologies could not only eliminate the need to remember and manage passwords, but also greatly reduce the odds of an unauthorized login. Auth0 also launched Passwordless, a product that enables users to login with nothing but their phone and email address.
The Bottom Line
Security breaches have become alarmingly common, but even the victims of cybersecurity incidents haven’t stepped up their security measures. The good news is that new technologies are making it easier than ever to protect your own personal data and that of employees from cybersecurity threats. The key is properly implementing these technologies and ensuring that employees receive enough training to actually use them.
Sign up for Jungle Disk to access a comprehensive cybersecurity suite that’s specifically designed for small businesses with between two and 250 employees.